BRICKSTORM Malware Revealed: Key Impacts of a Stealthy Cyber Threat

➤Summary
BRICKSTORM malware has emerged as one of the most concerning stealth threats highlighted in recent global cyber threat intelligence roundups. Identified in late 2025 reporting, this malware demonstrates how modern attackers prioritize persistence, evasion, and intelligence gathering over noisy, destructive attacks. Unlike traditional malware, BRICKSTORM is designed to operate quietly inside compromised environments, often remaining undetected for long periods while harvesting data and maintaining remote access.
Security analysts tracking underground activity note that BRICKSTORM malware frequently appears in Dark web report discussions linked to espionage-style campaigns rather than quick financial crime.
This article explores how BRICKSTORM malware works, why it is difficult to detect, and how organizations can protect themselves using proactive monitoring and a Dark web monitoring solution 🧠.
What Is BRICKSTORM Malware
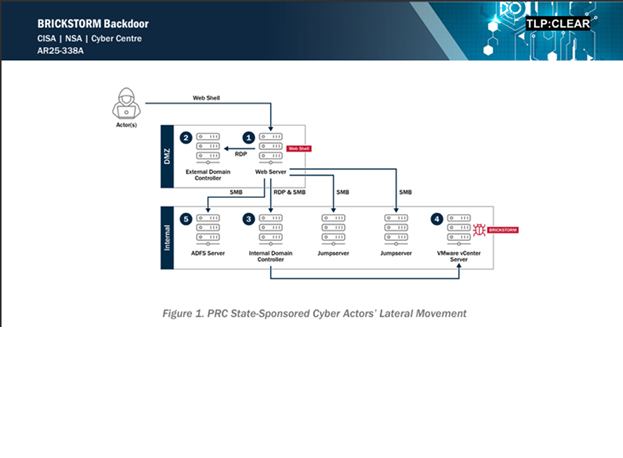
BRICKSTORM malware is a sophisticated backdoor framework believed to be used in targeted cyber operations. It is not mass-distributed like common ransomware or banking trojans. Instead, it is selectively deployed against high-value targets, including enterprises, government-linked infrastructure, and service providers. Researchers describe it as modular malware that allows attackers to customize capabilities based on their objectives, such as reconnaissance, credential harvesting, or lateral movement. Because of its controlled deployment and minimal footprint, BRICKSTORM malware aligns with advanced persistent threat behavior rather than opportunistic cybercrime.
How BRICKSTORM Malware Works
BRICKSTORM malware works by establishing a covert communication channel between the infected system and attacker-controlled infrastructure. Initial access is often achieved through compromised credentials, exposed services, or trusted third-party software. Once deployed, the malware installs itself in a way that mimics legitimate system processes, helping it evade detection. It then periodically communicates with its command-and-control server, sending system information and receiving instructions. These instructions may include executing commands, downloading additional modules, or modifying configurations. Because BRICKSTORM malware operates with low network noise and limited resource usage, it can remain hidden for months while quietly collecting intelligence 🕵️.
Why BRICKSTORM Malware Is So Hard to Detect
The stealthy design of BRICKSTORM malware makes it particularly challenging for traditional security tools. Signature-based antivirus solutions may fail to flag it because each deployment can be slightly customized. Behavioral detection is also difficult, as the malware’s activity closely resembles legitimate administrative tasks. Additionally, BRICKSTORM often uses encrypted communication channels, further obscuring its presence. Several Dark web report analyses indicate that victims typically discover infections only after secondary indicators appear, such as unusual account behavior or leaked data being advertised underground 😟.
Connection to Global Cyber Threat Trends
According to global cyber threat reporting, BRICKSTORM malware fits into a broader shift toward long-term, intelligence-driven cyber operations. Attackers are increasingly focused on persistence and data access rather than immediate monetization. This trend has been observed in multiple Case Study Dark web monitoring investigations, where compromised environments were quietly exploited over time before any public exposure. Such campaigns often overlap with geopolitical tensions and strategic targeting, making early detection critical.
Dark Web Activity and Underground Discussions
Threat intelligence researchers have observed references to BRICKSTORM malware in private forums and invite-only channels rather than open marketplaces. This suggests restricted access and controlled usage by skilled operators. In several Dark web report summaries, mentions of BRICKSTORM were linked to discussions about infrastructure access, data exfiltration methods, and operational security🌐.
Question: Is BRICKSTORM Malware Used for Ransomware?
Answer: No, BRICKSTORM malware is not primarily used for ransomware attacks. Its main purpose is stealthy access, surveillance, and long-term control rather than immediate financial extortion.
Real-World Impact on Organizations
Organizations affected by BRICKSTORM malware face significant risks even if no immediate damage is visible. Stolen credentials, internal documentation, and network maps can later be used for larger attacks or sold to other threat actors. In some Case Study Dark web monitoring examples, initial BRICKSTORM infections were followed months later by data leaks or destructive attacks carried out by different groups. This delayed impact makes the malware especially dangerous, as organizations may believe they are secure while attackers are still present.
Practical Checklist: How to Defend Against BRICKSTORM Malware
To reduce exposure to BRICKSTORM malware, security teams should implement the following checklist:
- Enforce strong access controls and regularly rotate credentials.
- Monitor outbound network traffic for unusual encrypted connections.
- Audit system processes for anomalies that mimic legitimate services.
- Deploy endpoint detection tools with behavioral analytics.
- Use a Dark web monitoring solution to identify early mentions of compromised assets 🛡️.
This checklist has proven effective in multiple Case Study Dark web monitoring investigations where early intervention limited attacker dwell time.
The Role of Dark Web Monitoring Solutions
A comprehensive Dark web monitoring solution provides visibility beyond the network perimeter. By tracking underground forums, leak sites, and private channels, organizations can detect signs of BRICKSTORM malware activity before public disclosure or operational damage occurs. Integrating these insights with internal telemetry allows defenders to prioritize investigations and respond proactively 📊.
Expert Insight on Stealth Malware
Cyber threat analysts emphasize that malware like BRICKSTORM represents a new normal. One expert noted, “The most dangerous threats today are not the loud ones. They are the quiet tools that sit inside networks, learning and waiting.” This perspective reinforces the importance of continuous monitoring, threat intelligence, and assumption of breach mentality in modern defense strategies 🔐.
Why BRICKSTORM Malware Matters in 2025 and Beyond
As organizations adopt cloud services, remote administration, and automation, attackers gain more opportunities to hide malicious activity within legitimate workflows. BRICKSTORM malware demonstrates how advanced threats exploit trust, complexity, and visibility gaps. Without proactive detection and intelligence-driven security, similar campaigns will continue to succeed unnoticed.
Conclusion
BRICKSTORM malware is a clear example of how cyber threats are evolving toward stealth, persistence, and intelligence gathering. Its ability to remain hidden while enabling long-term access makes it a serious risk for organizations of all sizes. By combining internal security controls with external intelligence from Dark web report analysis and a robust Dark web monitoring solution, defenders can significantly reduce their exposure.
Discover much more in our complete guide
Request a demo NOW
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourselfsssss.
