Aviation Data Breach Revealed: Key Insights into Israel Aerospace Cyberattack

➤Summary
The Aviation data breach reported in late October 2025 sent ripples through Israel’s aerospace industry, exposing how deeply connected digital systems have become within the defense ecosystem. According to early intelligence reports and breach monitoring services, a small contractor named Oz Aviation Ltd appears to have been compromised, with internal data allegedly posted on a dark web forum on 27 October 2025. While investigations are ongoing, this event underscores the rising threat of Israel aerospace cyberattacks and the urgent need for proactive dark web monitoring. ✈️💻
Background: The Growing Wave of Aviation Data Breaches
The global aviation industry faces a surge of targeted cyberattacks, and Israel’s aerospace sector is no exception. The Aviation data breach affecting Oz Aviation Ltd highlights the persistent vulnerabilities in third-party supply chains. Subcontractors—often smaller firms handling logistics, maintenance, or software integrations—serve as indirect entry points for attackers seeking to reach larger defense companies.
The alleged attacker, using the handle CyberToufan02, reportedly shared samples of data on a forum post at Darkforums.st, accompanied by claims about corporate involvement with major aerospace entities. Authorities have not verified the authenticity of these allegations, but the presence of sensitive files alone raises red flags about the supply chain’s digital hygiene. 🧠
📸 [Forum Post Proof]
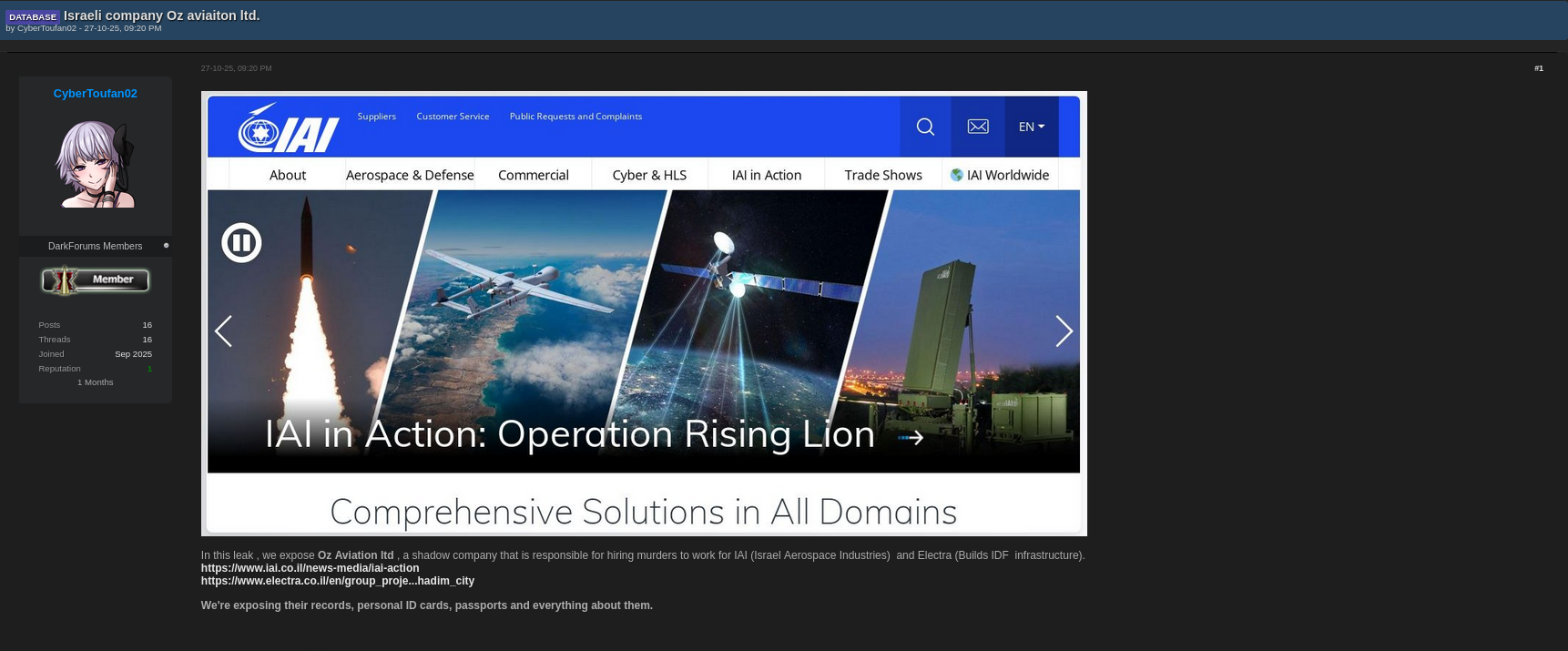
Understanding the Israel Aerospace Cyberattack Threat Landscape
A Israel aerospace cyberattack often combines multiple layers: phishing, supply-chain infiltration, and insider reconnaissance. In this case, the Aviation data breach may have been enabled by a compromised endpoint or exposed remote-access credential. Threat actors targeting the aerospace sector usually pursue:
- Intellectual property such as design blueprints or R&D data.
- Operational logistics that reveal flight schedules or infrastructure layouts.
- Employee credentials for deeper penetration or social engineering.
Cybersecurity researcher Dr. Lior Ben-David explains:
“Attackers no longer need to strike at the main defense contractor. They compromise smaller subcontractors like Oz Aviation, who often have access to sensitive systems through maintenance or software pipelines.”
This mirrors tactics seen worldwide, where state-linked and financially motivated groups exploit the weakest link in interconnected networks.
What Makes Aviation Data Breaches Unique ✈️
Unlike typical corporate leaks, an Aviation data breach can have national security implications. The aerospace industry deals with proprietary technologies, flight control systems, and defense-grade infrastructure. Any exposure—even partial—can:
- Reveal supplier hierarchies.
- Undermine competitive advantages.
- Allow foreign intelligence to reverse-engineer sensitive processes.
Furthermore, aviation networks often operate across multiple vendors and countries, expanding the attack surface. Once an adversary infiltrates one contractor, they can pivot laterally through email chains, shared documentation platforms, or software integration layers.
What Kind of Data Might Be Affected?
While investigators have not confirmed the full dataset, typical aviation-related breaches expose:
- Employee contact lists and access credentials.
- Internal emails or contracts linking suppliers to larger defense projects.
- Procurement records, shipment schedules, or maintenance logs.
Even without classified files, this data can facilitate spear phishing attacks, identity fraud, or industrial cyber espionage. For example, a malicious actor might impersonate a known supplier to deliver a weaponized PDF invoice, gaining deeper access through deception.
How darknetsearch.com Can Help to Block the Impact of Data Breach 🛡️
In today’s interconnected digital landscape, the ability to detect and respond early makes the difference between containment and catastrophe. Here’s how darknetsearch.com can help to block the impact of data breach incidents like this one:
- Real-time Monitoring: The platform continuously scans dark web forums, Telegram channels, and leak marketplaces for domain mentions, credentials, and project names.
- Automated Alerts: When a company’s email, IP, or keyword appears in breach chatter, users receive immediate alerts—often before leaks go public.
- Verification & Takedowns: Built-in algorithms confirm dataset authenticity, reducing false positives, and supporting takedown requests for stolen data.
- Integration with SOC systems: Enables incident response teams to correlate dark web intelligence with internal logs for rapid remediation.
- Strategic Insights: Reports include threat actor profiling and data-lifecycle tracking, giving CISOs actionable insights for defense planning.
🚀 Practical Tip: Integrate dark web monitoring into your SOC workflow. Set automated alerts for your company’s domain and project codenames to identify exposure before attackers exploit it.
Why the Israel Aerospace Cyberattack Matters Beyond Borders 🌍
The aerospace supply chain extends globally. A breach in one small contractor can expose blueprints or specifications relevant to multiple allied nations. Moreover, this Israel aerospace cyberattack could inspire similar campaigns targeting European and North American partners involved in defense manufacturing.
In 2025, cyber espionage has become as strategic as kinetic warfare. Threat actors exploit open-source intelligence (OSINT) and dark web data to map out entire industrial ecosystems. Once sensitive credentials or project references appear online, attackers often cross-reference them with past leaks to craft multi-layered infiltration campaigns.
Detection and Response Checklist 🧾
To help organizations respond quickly, here’s a practical checklist inspired by standard incident response frameworks:
- Validate authenticity: Confirm whether the leaked data belongs to your organization.
- Reset credentials: Immediately change passwords and enforce MFA across endpoints.
- Inspect logs: Check for abnormal login attempts and privilege escalations.
- Notify partners: Inform third parties who might share systems or credentials.
- Engage forensic experts: Collect evidence properly for law enforcement or insurance.
- Enhance monitoring: Use platforms like darknetsearch.com to identify secondary leaks or related chatter.
- Update policies: Patch vulnerabilities and revise access control protocols.
These steps not only help contain the immediate risk but also strengthen long-term cyber resilience.
Common Questions About Aviation Data Breaches ❓
Q: Are aviation contractors at higher risk than other industries?
A: Yes. Their networks handle operational data tied to national security and rely on third-party suppliers, making them prime targets for espionage and ransomware groups.
Q: Can a company prevent an Israel aerospace cyberattack entirely?
A: No system is 100% immune, but layered defenses—network segmentation, dark web monitoring, and strong authentication—dramatically reduce impact and exposure.
Q: What happens if leaked data is already online?
A: Work with intelligence and legal teams to request takedowns, change credentials, and monitor darknet chatter for reuse of compromised information.
The Role of Cyber Intelligence in Preventing Future Attacks 🧠
Cyber intelligence transforms raw threat data into actionable defense. By connecting breach chatter to verified entities, analysts can anticipate attack patterns. Platforms like darknetsearch.com enable defenders to stay ahead of threat actors by visualizing relationships between breaches, usernames, and domains across time.
Integrating such intelligence into existing SOC operations helps companies not just react, but predict the next move. Early detection reduces dwell time—often the single most important factor in preventing data loss escalation.
Expert Insight: Strengthening the Supply Chain 🔐
Industry expert Dana Mor, a senior threat intelligence analyst, notes:
“Cybersecurity can’t stop at the borders of a company. Each partner in the aerospace ecosystem must enforce zero-trust access, continuous monitoring, and shared intelligence feeds to ensure collective defense.”
This insight reinforces the reality that cybersecurity today is a shared responsibility. The Oz Aviation incident is less about one company and more about systemic vulnerability within interconnected networks.
Conclusion: Building a Stronger Digital Defense ✈️🛡️
The Aviation data breach involving Oz Aviation Ltd serves as a cautionary reminder: cybersecurity in aerospace is not optional—it’s mission-critical. As the Israel aerospace cyberattack landscape grows more sophisticated, only those companies that adopt proactive intelligence and real-time monitoring will stay ahead.
By leveraging tools like darknetsearch.com, organizations can detect early warning signs, minimize data exposure, and act before adversaries weaponize stolen information.
Don’t wait for the next breach headline—start monitoring, patching, and defending today.
Discover much more in our complete guide.
Request a demo NOW.
Your data might already be exposed. Most companies find out too late. Let ’s change that. Trusted by 100+ security teams.
🚀Ask for a demo NOW →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


