Adidas Data Breach Exposed: 815,000 Extranet Records Leaked

➤Summary
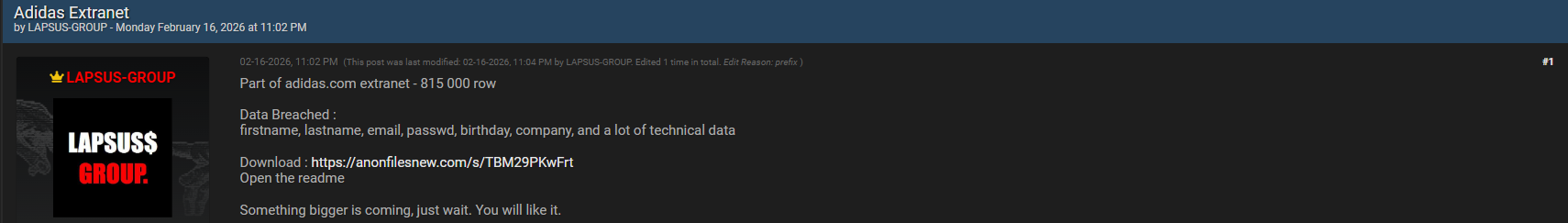
The alleged adidas data breach has quickly become one of the most discussed cybersecurity incidents of early 2026, raising serious concerns about third-party portals, identity exposure, and credential reuse. On 16 February 2026, the Kaduu team identified a massive leaked database linked to the Adidas extranet while conducting routine Dark web monitoring on underground forums. The dataset, allegedly published on BreachForums by an actor using the name “LAPSUS-GROUP,” contains more than 815,000 rows of sensitive records tied to corporate and partner access.
This Adidas data breach highlights how exposed assets outside the main website infrastructure can still create large-scale security and reputational risks. In this darknetsearch.com article, we break down what happened, what data was compromised, why it matters, and how organizations can strengthen data breach detection using modern dark web solution strategies. 🔐
What We Know About the Adidas Extranet Leak
According to findings shared by the Kaduu team, the compromised database was discovered during routine monitoring of dark web forums, specifically on BreachForums. The author claimed the data was “Part of adidas.com extranet – 815 000 row,” strongly suggesting an internal or partner-facing platform rather than the public Adidas website. The Adidas data breach does not appear to be the result of a direct website hack but rather an exposed database or misconfigured system accessible through unauthorized means. Such incidents are increasingly common as organizations expand their digital ecosystems with vendors, partners, and remote access tools. This case underlines the importance of exposed asset discovery across all digital surfaces, not just consumer-facing domains. 🕵️♂️
Timeline and Discovery of the Breach
The database was published on 16 February 2026 by a threat actor operating under the alias LAPSUS-GROUP, a name that immediately drew attention due to its similarity to previously known threat groups. The Kaduu team detected the leak during scheduled Dark web monitoring, scanning BreachForums for newly shared datasets related to high-profile brands. Once identified, the data was analyzed to confirm structure, volume, and relevance to Adidas extranet systems. Early discovery through data breach detection allowed researchers to document the scope before the dataset could spread further across multiple marketplaces and Telegram channels. Early visibility is often the difference between controlled response and widespread exploitation. 🚨
What Data Was Compromised
The leaked Adidas extranet database reportedly includes a broad range of personal and technical information. Compromised data fields include:
- First name
- Last name
- Email address
- Password (format unknown, possibly hashed)
- Birthday
- Company affiliation
- Extensive technical metadata related to accounts and access
This type of information dramatically increases the risk of credential stuffing, phishing campaigns, and targeted social engineering attacks. In the context of the Adidas data breach, even hashed passwords can be dangerous when combined with reused credentials across corporate systems. The presence of company names suggests that partners, contractors, or B2B users may be among the affected population. 📧
Why This Adidas Data Breach Matters
You might ask: why is an extranet leak as serious as a consumer database breach? The answer is simple: extranet accounts often have elevated privileges. The alleged Adidas data breach potentially exposes access pathways into internal workflows, supply chain systems, or sensitive partner communications. Attackers value such data because it can be leveraged for lateral movement, ransomware staging, or further compromise. From a brand perspective, incidents like this also erode trust with partners and enterprise clients. From a regulatory standpoint, personal data exposure may trigger compliance obligations depending on jurisdictions involved. ⚠️
The Role of BreachForums and the Dark Web
BreachForums has become a central hub for cybercriminals to trade, sell, and showcase stolen data. In this case, the Adidas extranet database was allegedly shared openly, increasing its visibility and potential reach. Continuous Dark web monitoring is essential to identify these leaks early, especially when they involve well-known brands. Without dark web solution capabilities, organizations may remain unaware of breaches for weeks or months, allowing threat actors to monetize the data repeatedly. Platforms like BreachForums also act as reputational amplifiers, rapidly spreading breach claims across the cybercrime ecosystem. 🌐
Key Facts at a Glance
For quick reference and featured snippet optimization, here are the essential facts:
- Company affected: Adidas
- Source: BreachForums
- Published date: 16 February 2026
- Records exposed: ~815,000
- Data types: Personal, credentials, technical metadata
- Discovery method: Dark web monitoring by Kaduu team
How Attackers Can Exploit This Data
The Adidas data breach creates multiple exploitation scenarios. Stolen emails and passwords can be tested against VPNs, cloud services, and partner portals. Birthdays and company data enable convincing phishing emails tailored to professional contexts. Technical metadata may reveal system structures or software versions useful for follow-up attacks. This is why data breach detection alone is not enough; organizations must combine it with proactive exposed asset discovery to close gaps before attackers exploit them. 🔓
Data Breach Detection and Modern Defense Strategies
Effective data breach detection today relies on visibility beyond the perimeter. A modern dark web solution continuously scans forums, marketplaces, and private channels for mentions of brand assets, leaked credentials, and proprietary data. In the case of the Adidas data breach, early identification allowed researchers to assess scope and alert stakeholders faster. Detection should be paired with rapid response playbooks, password resets, and partner notifications. Organizations that invest in threat intelligence and dark web solution platforms reduce dwell time and long-term damage. 🛡️
Practical Checklist After an Extranet Breach
Here is a concise response checklist organizations can follow:
- Identify affected systems and users immediately
- Force credential resets and invalidate sessions
- Review extranet access controls and logs
- Notify partners and stakeholders transparently
- Enhance Dark web monitoring for recurring leaks
- Conduct full exposed asset discovery across subdomains and third parties
This checklist helps transform breach response from reactive panic into structured mitigation. ✔️
Internal and External Resources
For ongoing research into underground activity and breach disclosures, readers can explore internal threat intelligence resources in dark web monitoring platforms which tracks forums, marketplaces, and leaks in real time. For additional industry context and best practices, IBM’s security research provides high-authority insights into breach trends and response strategies at https://www.ibm.com/security/data-breach. 📚
Lessons Learned from the Adidas Data Breach
The Adidas data breach reinforces a critical lesson: security is only as strong as the weakest connected asset. Extranets, legacy portals, and partner systems often escape rigorous audits despite holding sensitive data. Continuous data breach detection, combined with exposed asset discovery, helps organizations maintain a real-time understanding of their risk landscape. Dark web solution platforms are no longer optional; they are a core component of modern cyber resilience. Brands that adopt this mindset can detect threats earlier, respond faster, and protect trust more effectively. 💡
Conclusion and Call to Action
The Adidas extranet incident is a clear reminder that high-profile brands remain prime targets, and that breaches often surface first in underground forums rather than official disclosures. By investing in Dark web monitoring, advanced data breach detection, and comprehensive exposed asset discovery, organizations can stay ahead of attackers instead of reacting after the damage is done. Don’t wait for your brand to appear on BreachForums to take action. 🚀 Discover much more in our complete guide and Request a demo NOW to see how a powerful dark web solution can protect your digital assets.
Disclaimer: DarknetSearch reports on publicly available threat-intelligence sources. Inclusion of an organization in an article does not imply confirmed compromise. All claims are attributed to external sources unless explicitly verified.
Discover how CISOs, SOC teams, and risk leaders use our platform to detect leaks, monitor the dark web, and prevent account takeover.
🚀Explore use cases →Q: What is dark web monitoring?
A: Dark web monitoring is the process of tracking your organization’s data on hidden networks to detect leaked or stolen information such as passwords, credentials, or sensitive files shared by cybercriminals.
Q: How does dark web monitoring work?
A: Dark web monitoring works by scanning hidden sites and forums in real time to detect mentions of your data, credentials, or company information before cybercriminals can exploit them.
Q: Why use dark web monitoring?
A: Because it alerts you early when your data appears on the dark web, helping prevent breaches, fraud, and reputational damage before they escalate.
Q: Who needs dark web monitoring services?
A: MSSP and any organization that handles sensitive data, valuable assets, or customer information from small businesses to large enterprises benefits from dark web monitoring.
Q: What does it mean if your information is on the dark web?
A: It means your personal or company data has been exposed or stolen and could be used for fraud, identity theft, or unauthorized access immediate action is needed to protect yourself.
Q: What types of data breach information can dark web monitoring detect?
A: Dark web monitoring can detect data breach information such as leaked credentials, email addresses, passwords, database dumps, API keys, source code, financial data, and other sensitive information exposed on underground forums, marketplaces, and paste sites.


